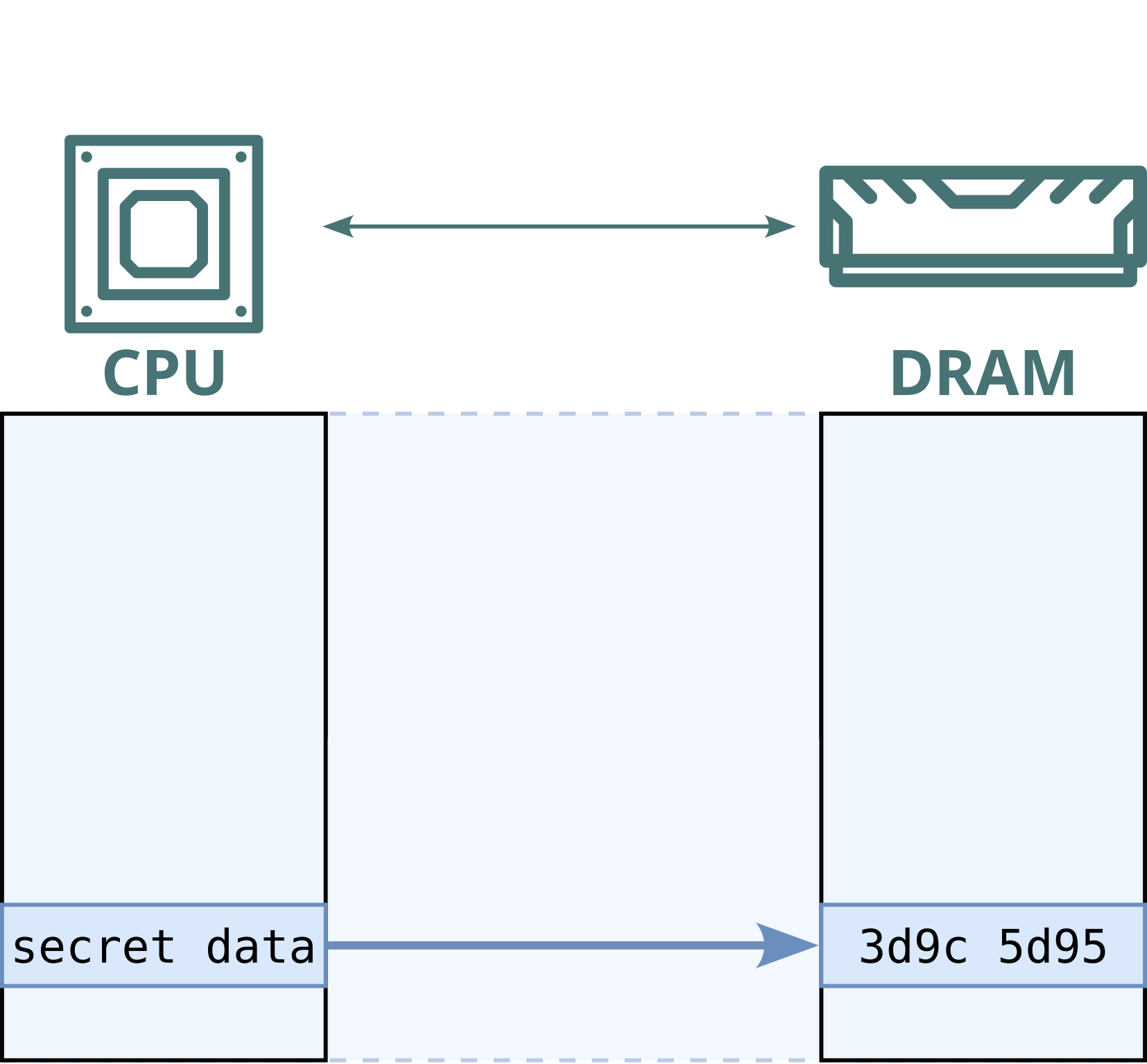
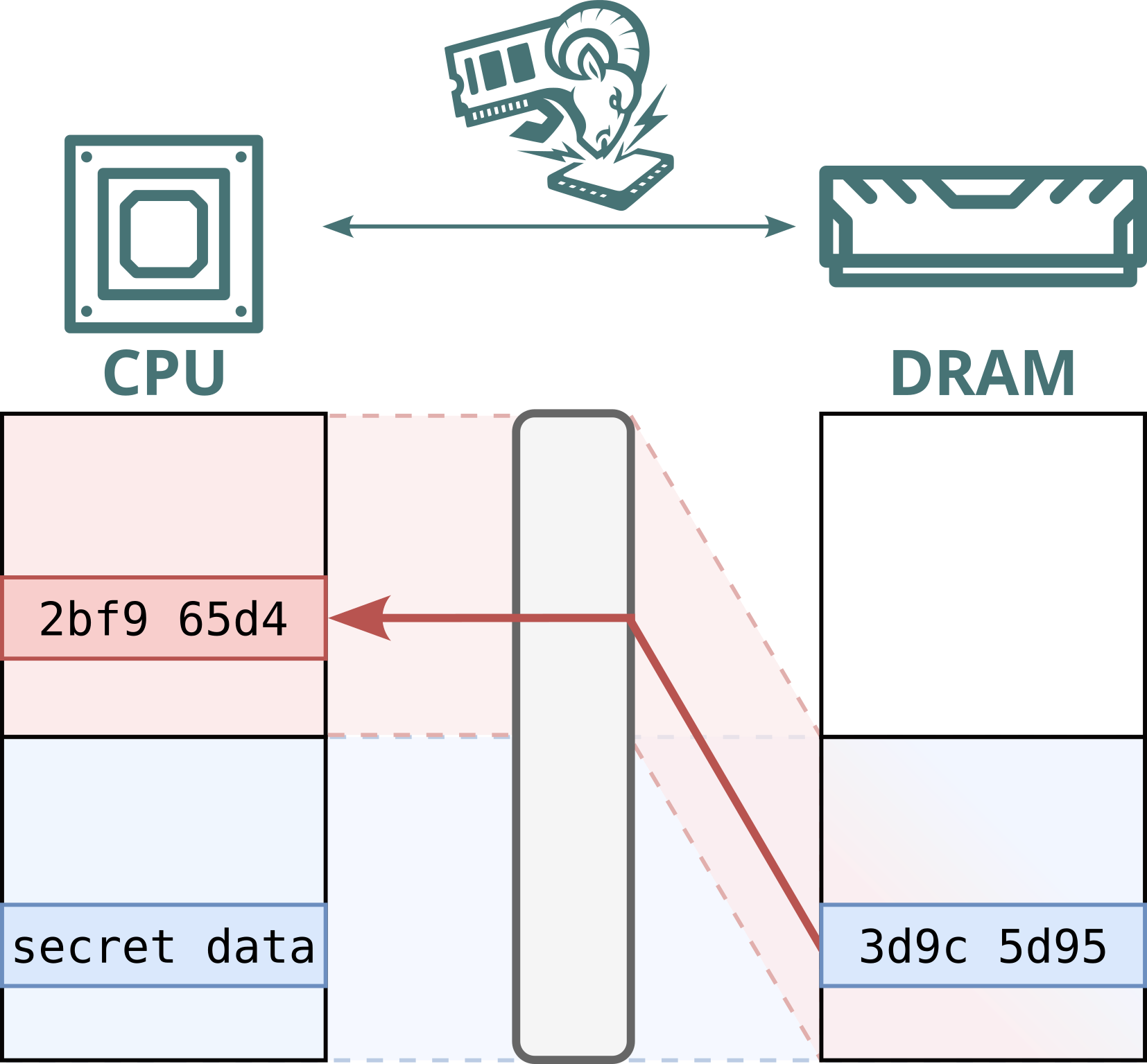
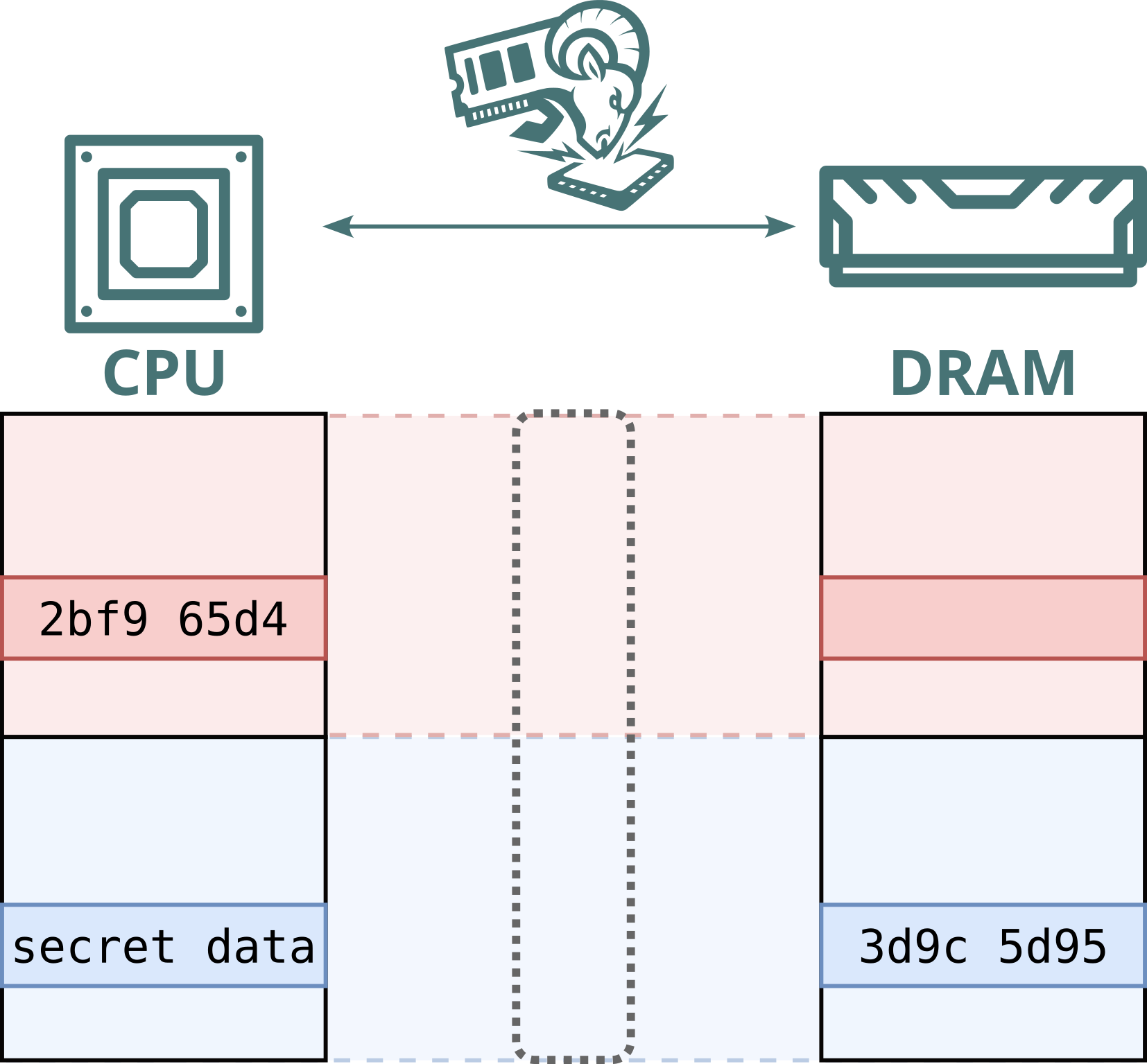
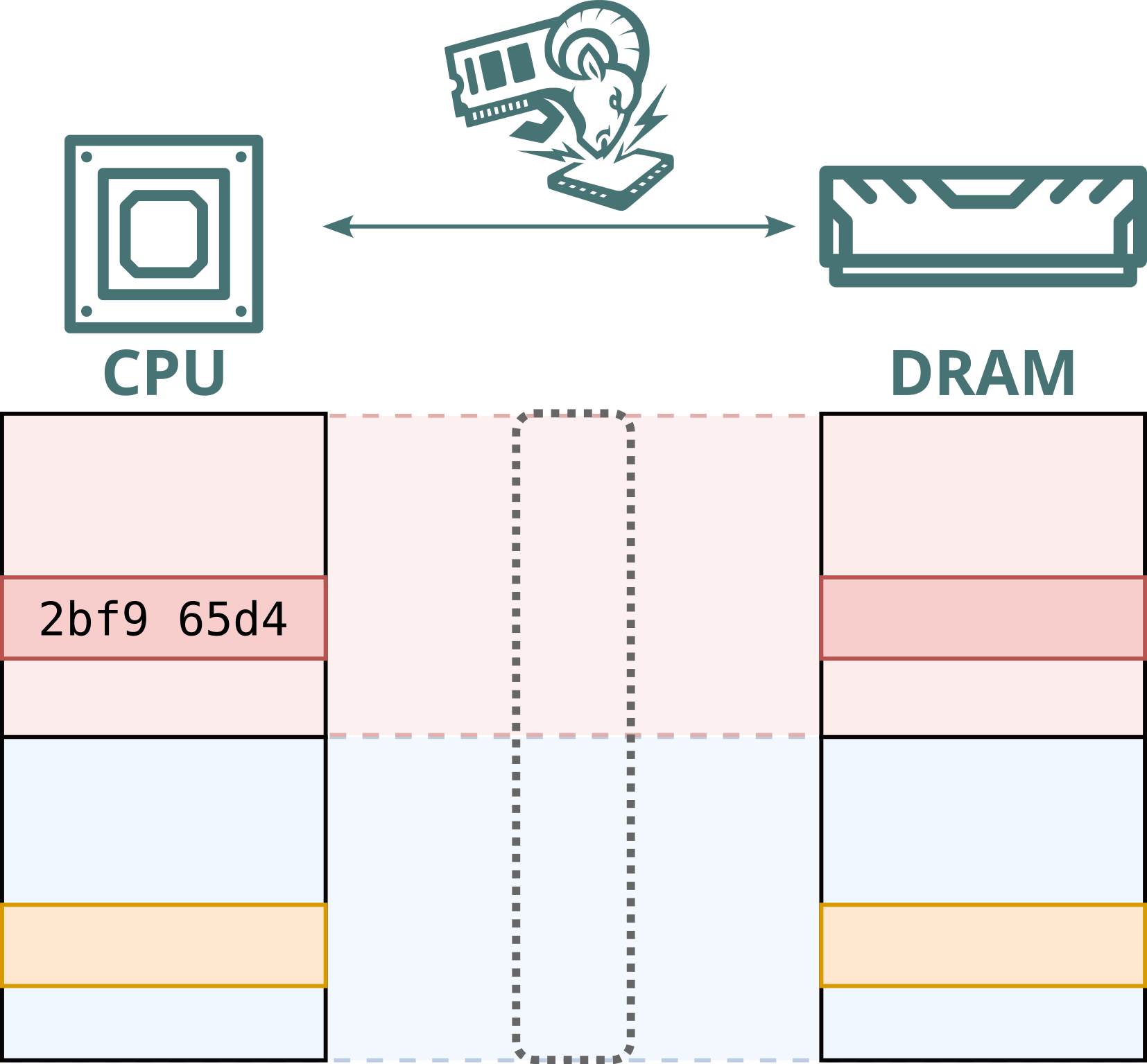
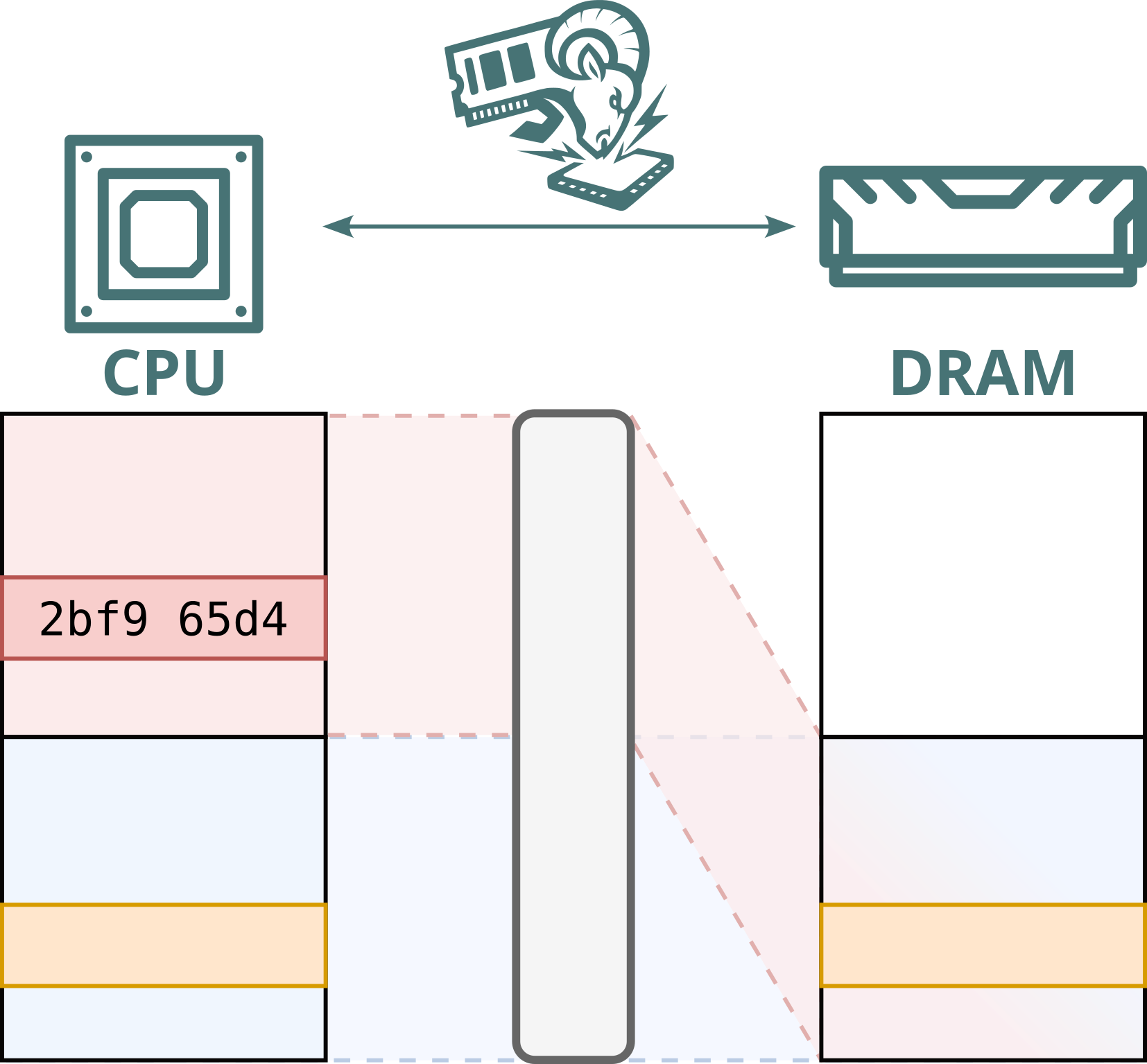
Modern computers use memory modules (DRAM) to store everything in use: from photos and passwords to credit card numbers. Public cloud providers increasingly deploy hardware-level memory encryption to protect this sensitive data. However, we previously showed that malicious memory modules, nicknamed “Bad RAM”, can bypass these protections by deliberately supplying false metadata during processor boot. In response, modern cloud systems now validate memory more strictly at startup.
Breaking Memory Encryption with Two-Faced DRAM
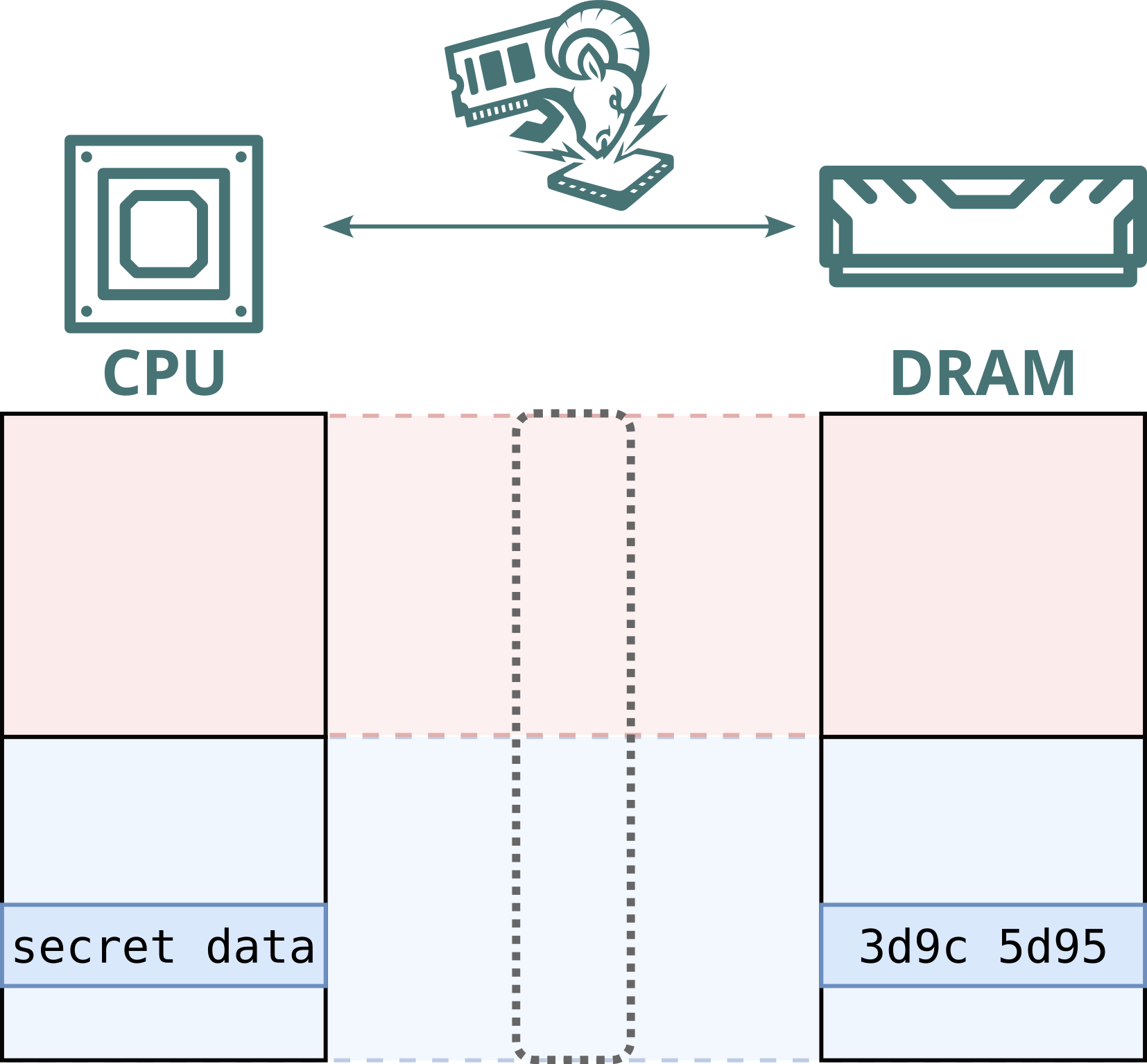
Battering RAM fully breaks cutting-edge Intel SGX and AMD SEV-SNP confidential computing processor security technologies designed to protect sensitive workloads from compromised hosts, malicious cloud providers, or rogue employees. Our stealthy interposer bypasses both memory encryption and state-of-the-art boot-time defenses, invisible to the operating system. It enables arbitrary plaintext access to SGX-protected memory, and breaks SEV’s attestation feature on fully patched systems. Ultimately, Battering RAM exposes the limits of today’s scalable memory encryption. Intel and AMD have acknowledged our findings, but defending against Battering RAM would require a fundamental redesign of memory encryption itself.
Building Battering RAM on a $50 Budget
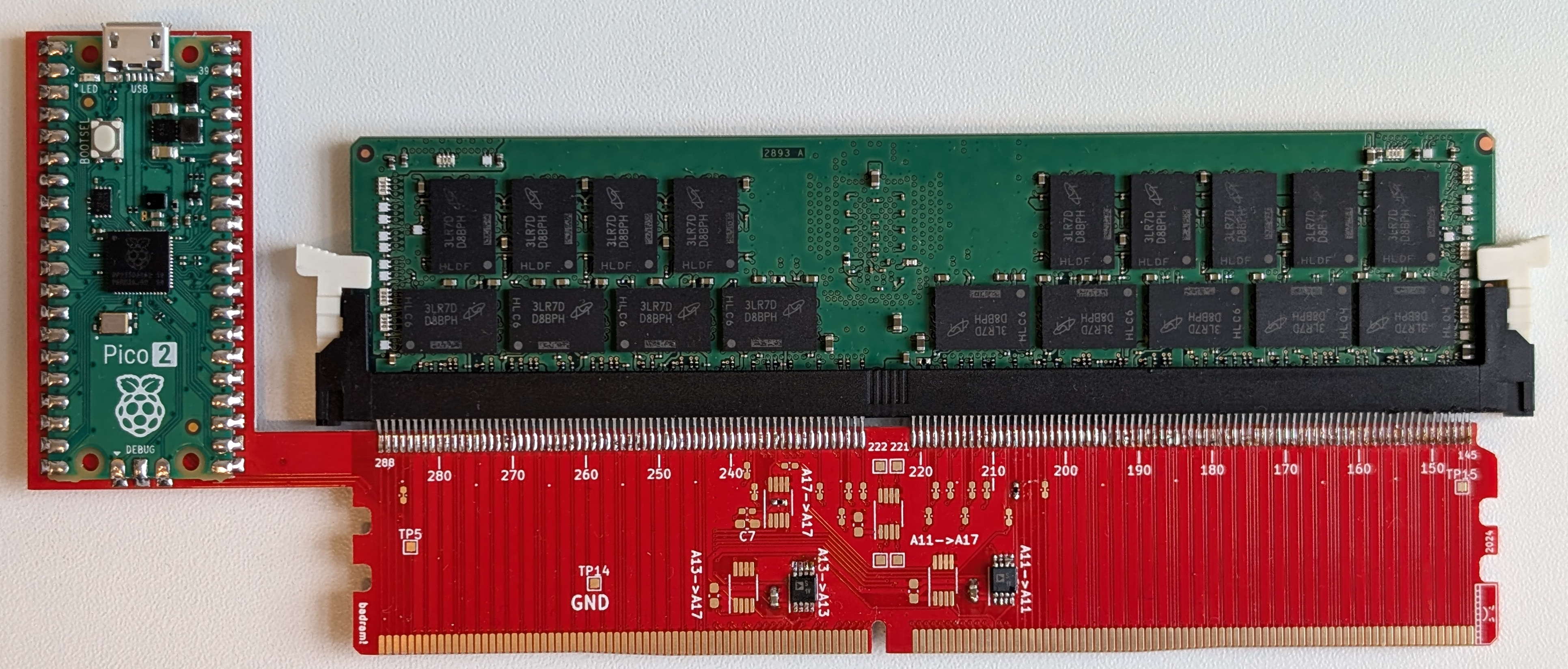
Unlike commercial passive interposers, which are exceedingly expensive and commonly cost over $100,000, we developed a custom-built interposer that uses simple analog switches to actively manipulate signals between the processor and memory, and can be built for less than $50.
All schematics and board files for our custom interposer are available as open source in our GitHub repository. The PCB is a standard 4-layer design and can be fabricated at any major PCB fabricator such as JLCPCB, PCBWay, or Eurocircuits.
| Component | Part Number | Cost | Qty. |
|---|---|---|---|
| PCB | Custom | $18.49 | 1 |
| DDR4 Connector | CONN-DDR4-288-SM | $16.00 | 1 |
| Microcontroller | Raspberry Pi Pico 1/2 | $4.00 | 1 |
| Switches | ADG902BRMZ | $4.04 | 2 |
| Voltage regulator | LD1117S25TR | $0.61 | 1 |
| Resistor | 0402, 1kOhm | <$0.01 | 2 |
| Capacitor | 0603, 100nF | $0.02 | 3 |
| Capacitor | 1206, 10μF | $0.18 | 1 |
| Total | $47.62 | ||
Battering RAM in Action
Questions and Answers
Battering RAM can affect all systems using DDR4 memory, but is especially relevant for "confidential computing" workloads running in public cloud environments.
Modern Intel and AMD x86 cloud processors feature built-in access control and memory encryption to keep private data safe, even from the company running the cloud. However, our research shows that these guarantees can be bypassed with a low-cost memory interposer, allowing a rogue cloud infrastructure provider or insider with limited physical access to compromise protected workloads.
Confidential computing aims to protect private data even from the cloud provider, using hardware-level access control and memory encryption. Even if someone accesses the memory, they should only see encrypted (garbled) data. Battering RAM uses a low-cost, custom-built memory interposer installed between the processor and memory to tamper with such encrypted memory. It requires only brief one-time physical access, which is realistic in cloud environments, considering, for instance:
- Rogue cloud employees;
- Datacenter technicians or cleaning personnel;
- Coercive local law enforcement agencies;
- Supply chain tampering during shipping or manufacturing of the memory modules.
Intel SGX and AMD SEV-SNP are two leading hardware-based trusted execution environments that enable secure cloud computations without needing to trust the cloud provider. They do this by enforcing strict access control and encrypting memory so that even if someone accesses it, they only see unreadable data.
AMD SEV and Intel SGX are widely offered by major cloud providers like like Amazon AWS, Google Cloud, Microsoft Azure, and IBM cloud. They also power privacy features in real-world applications like Signal, WhatsApp, and Chrome, and are used in sectors like healthcare to protect sensitive data.
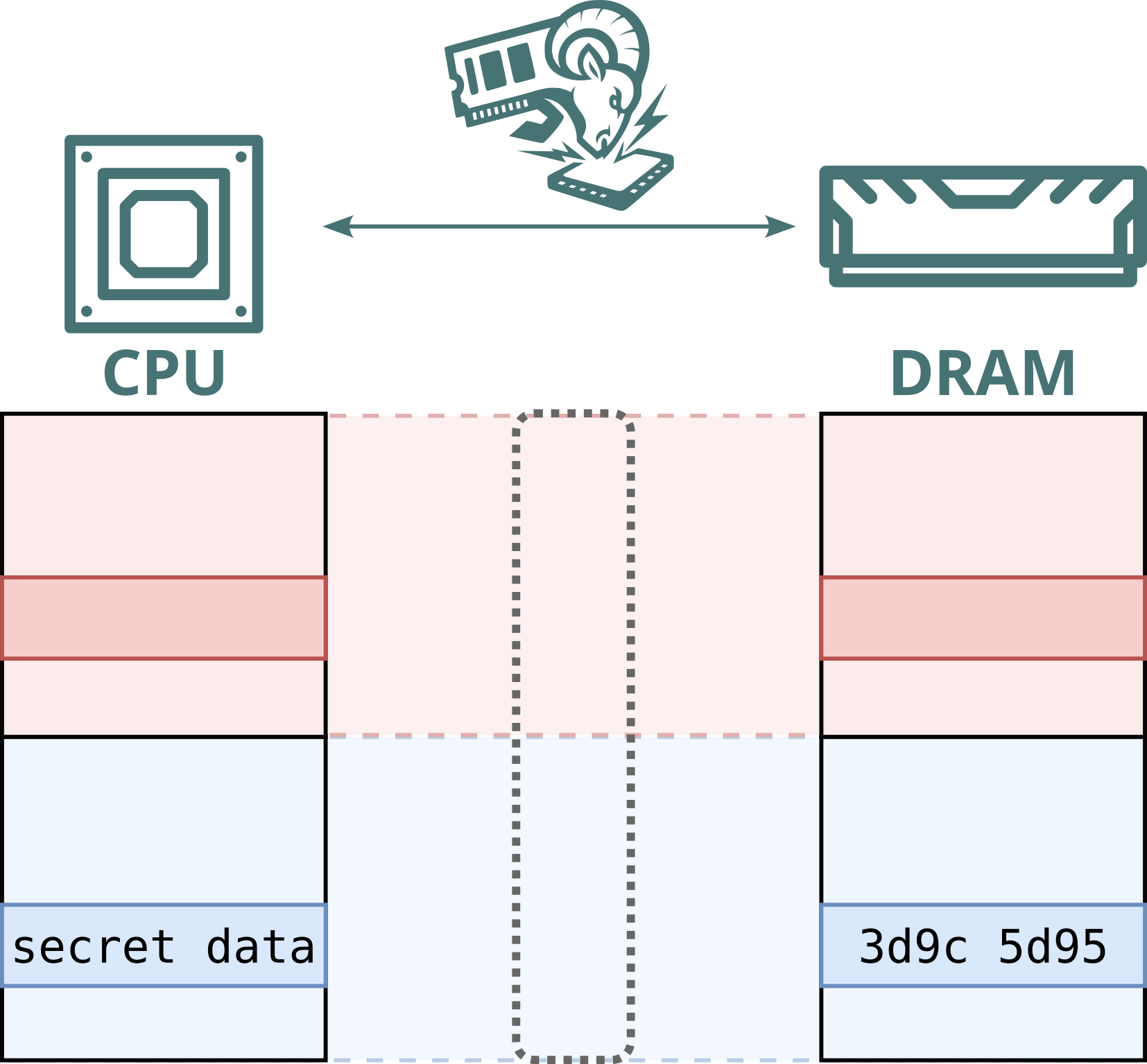
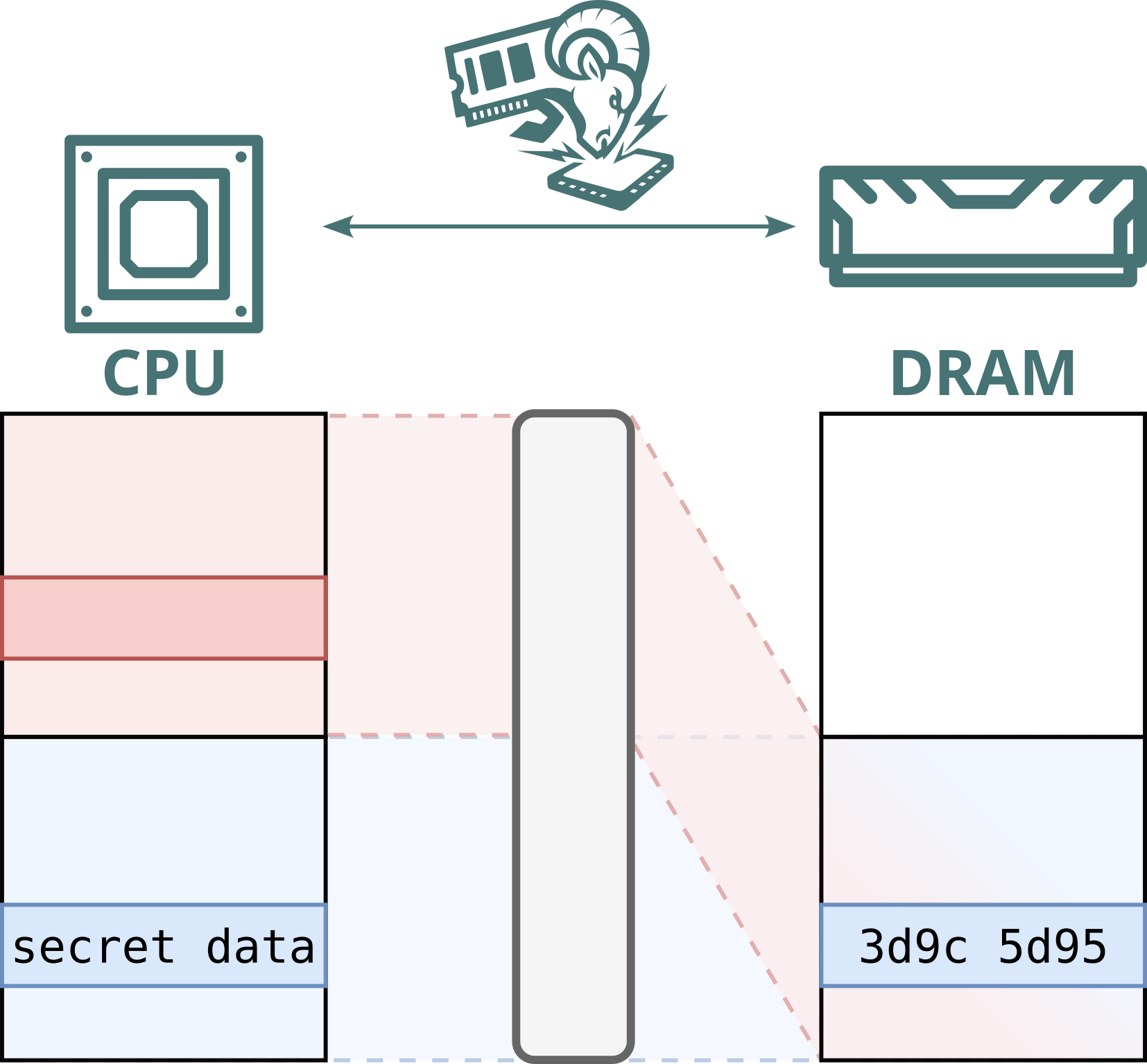
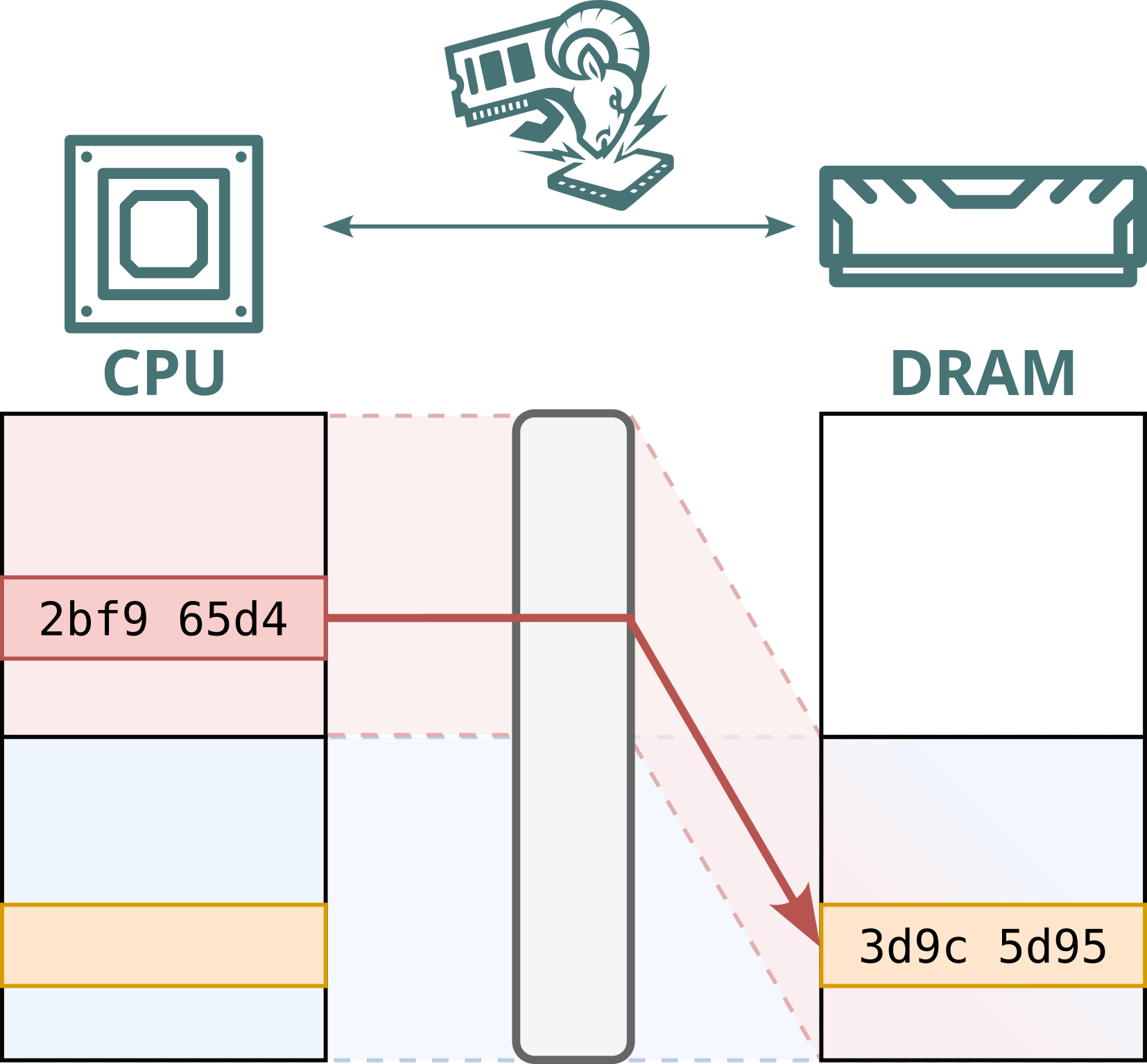
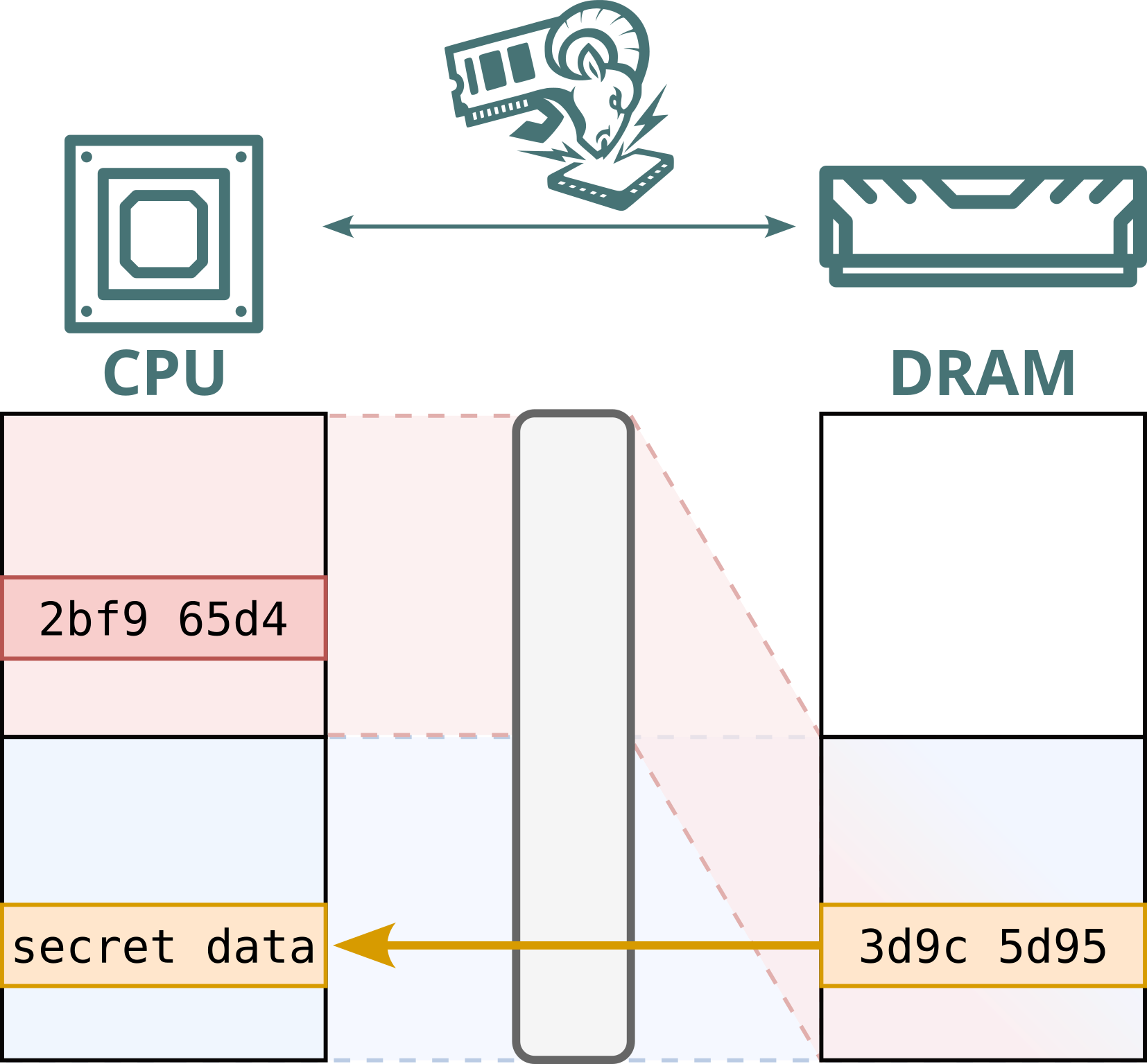
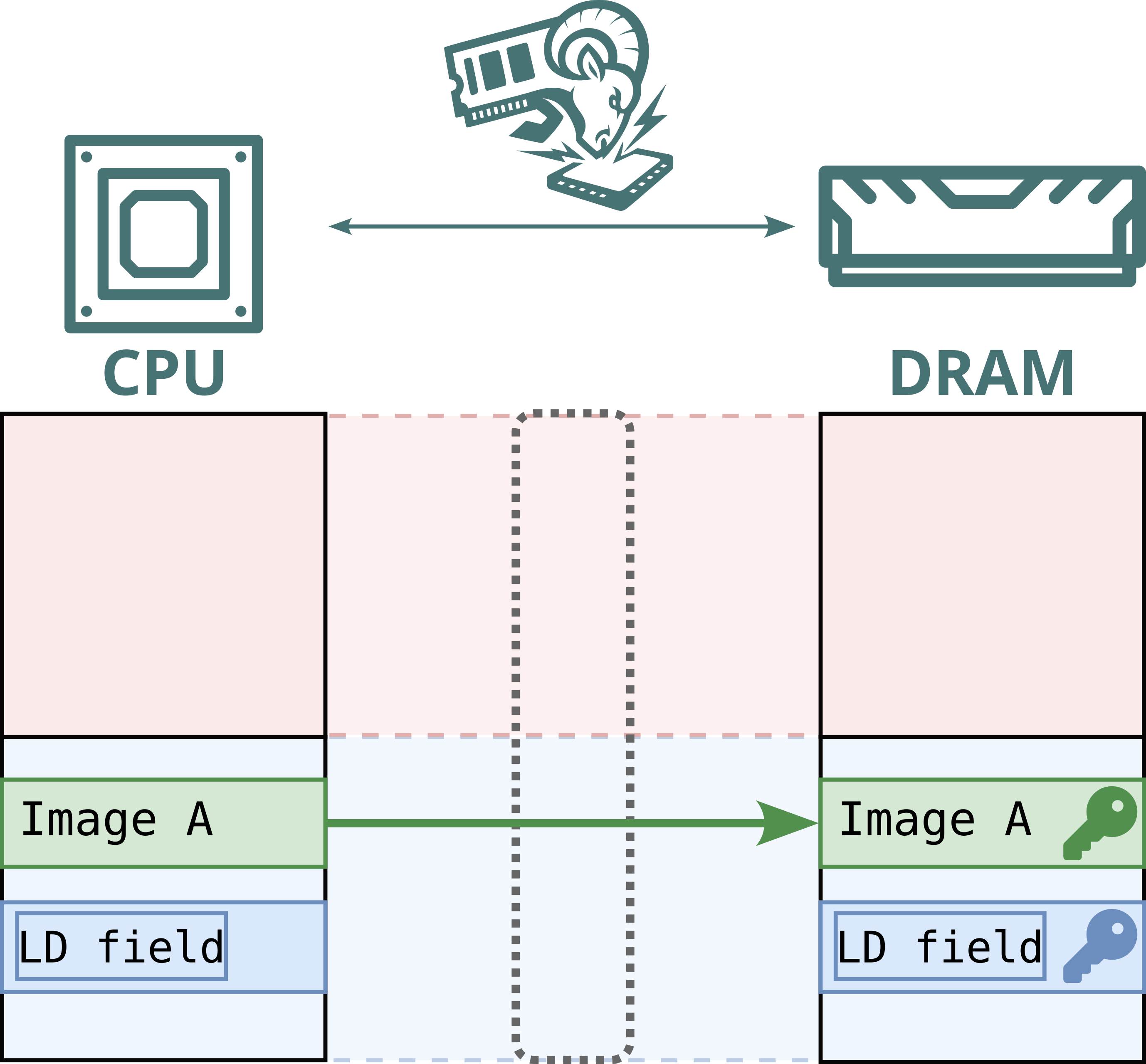
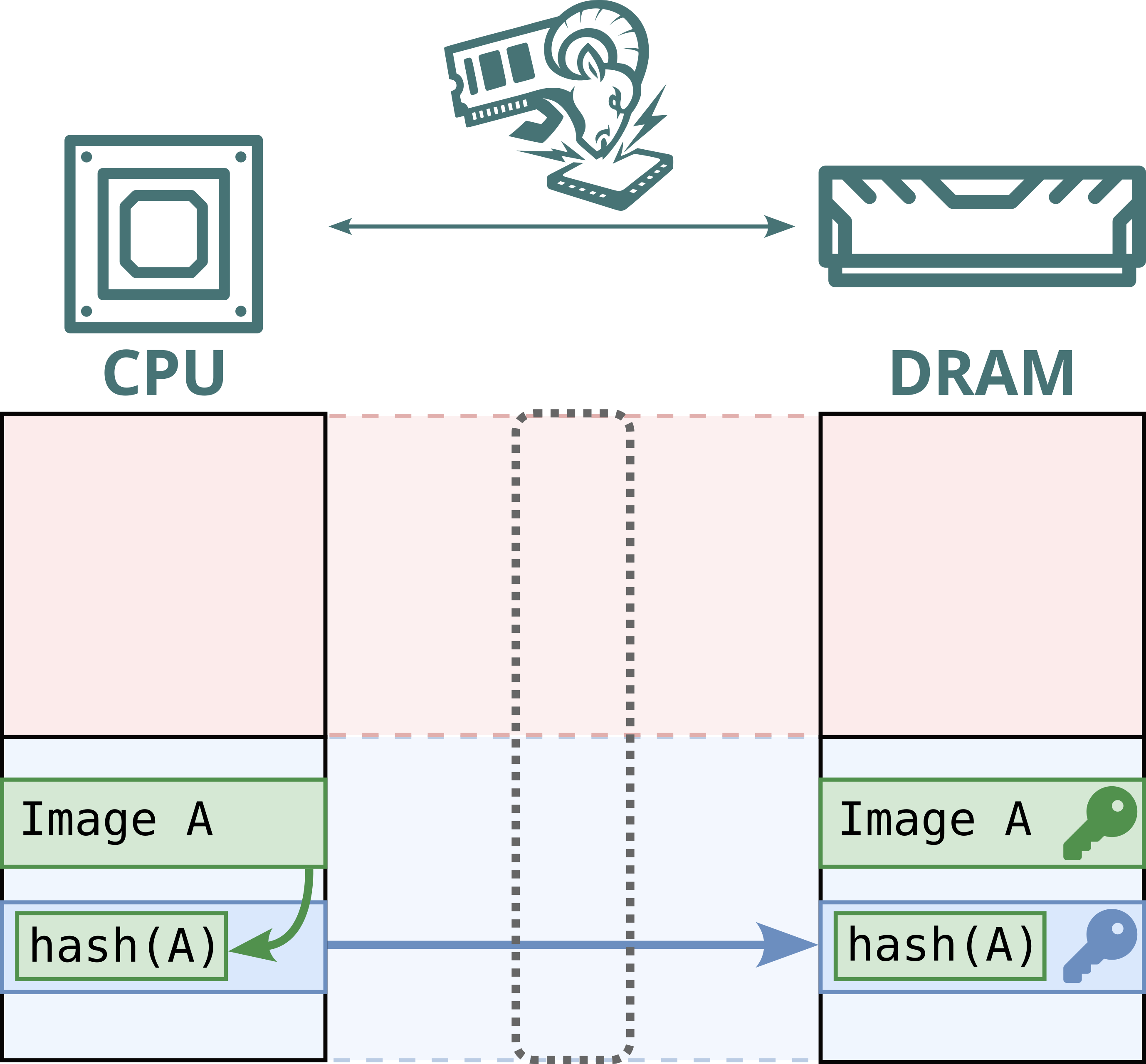
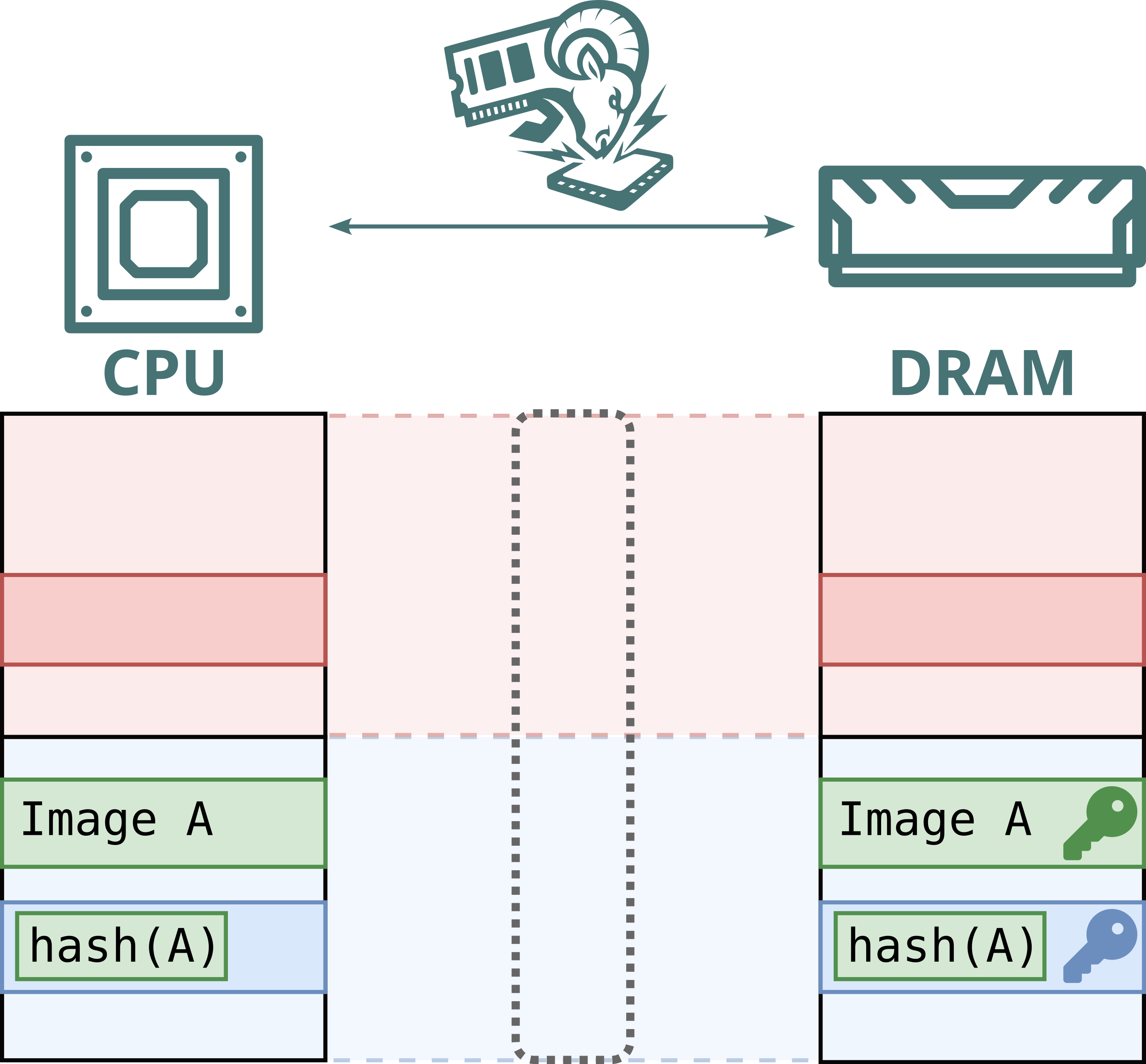
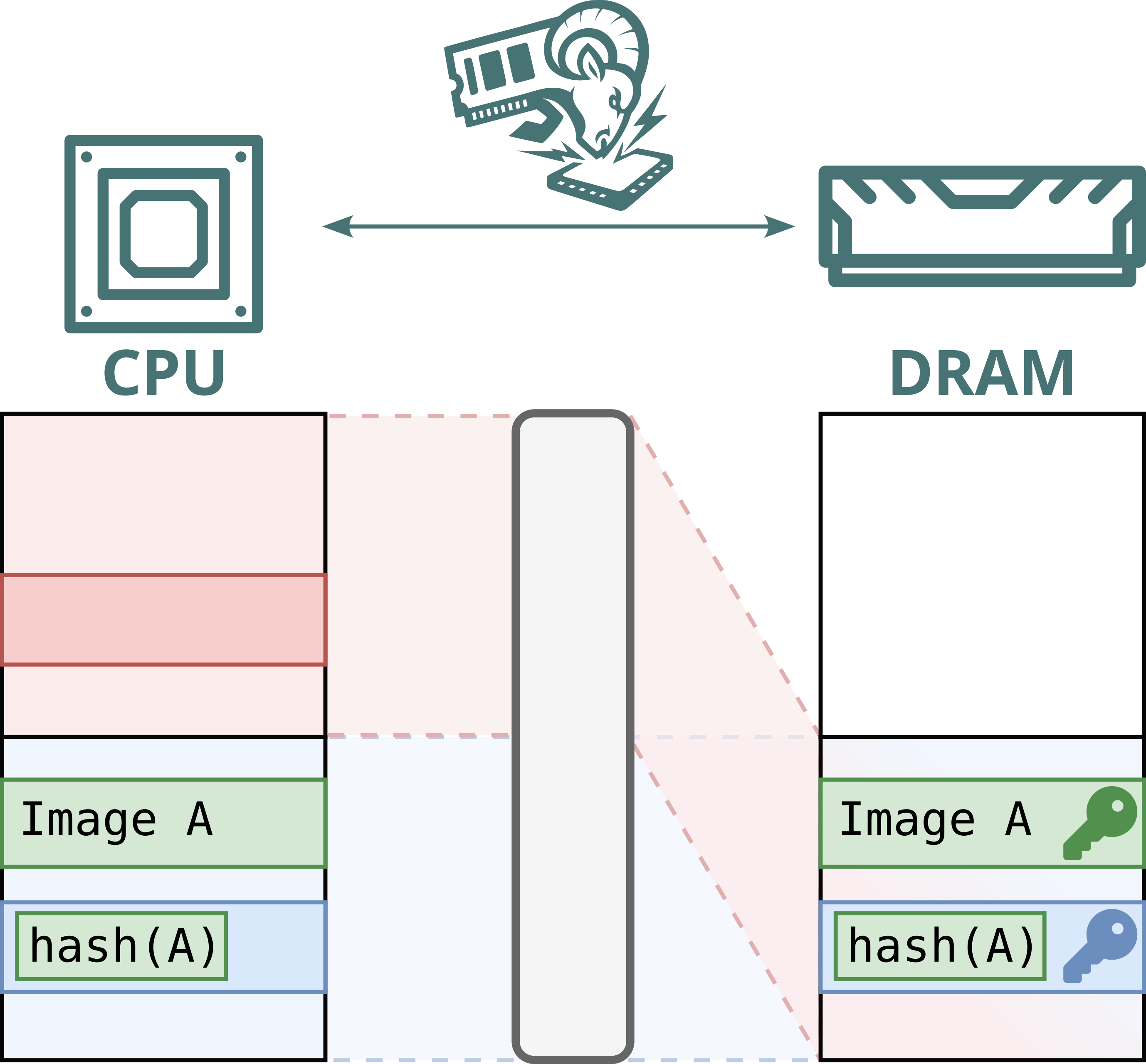
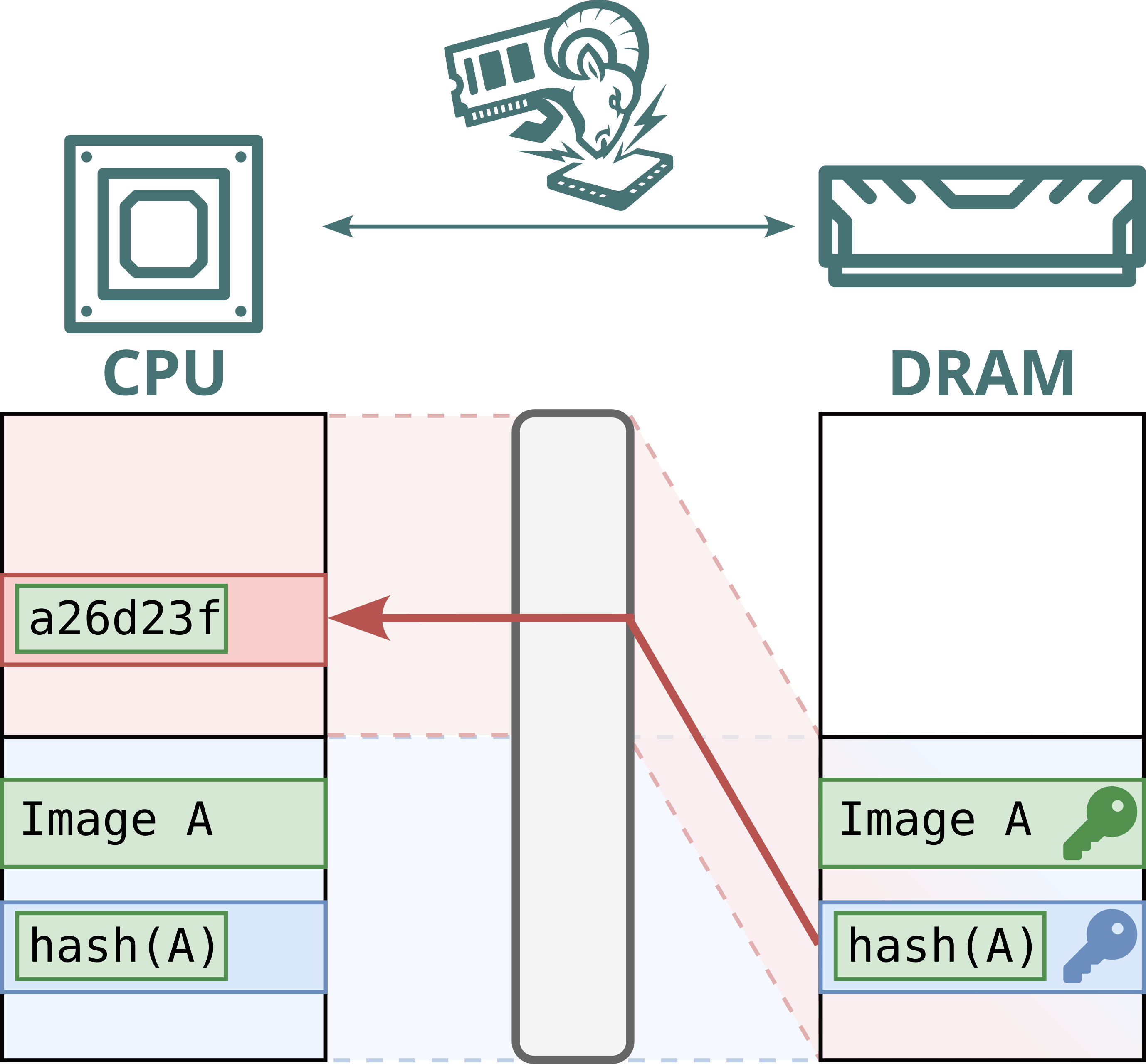
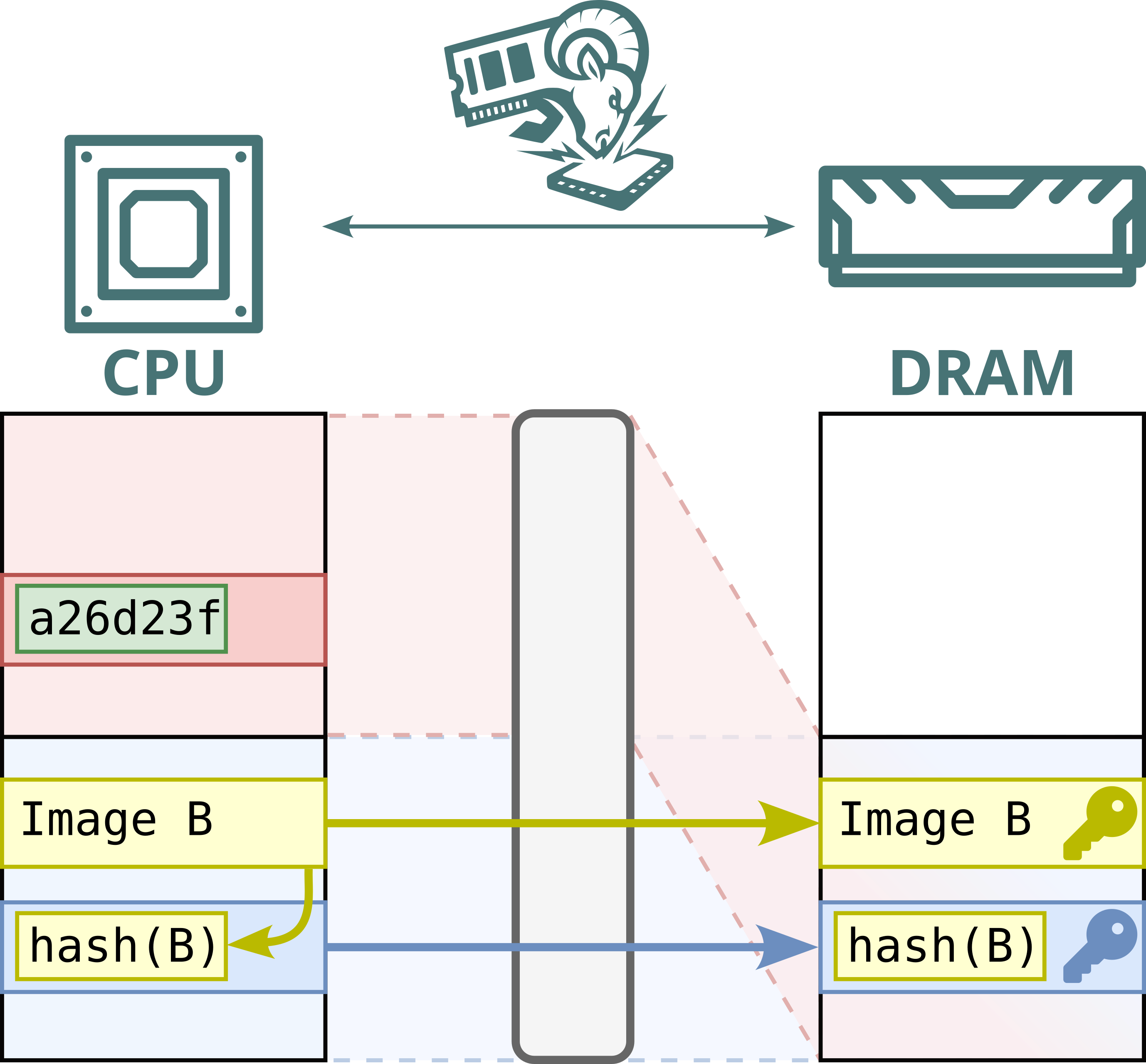
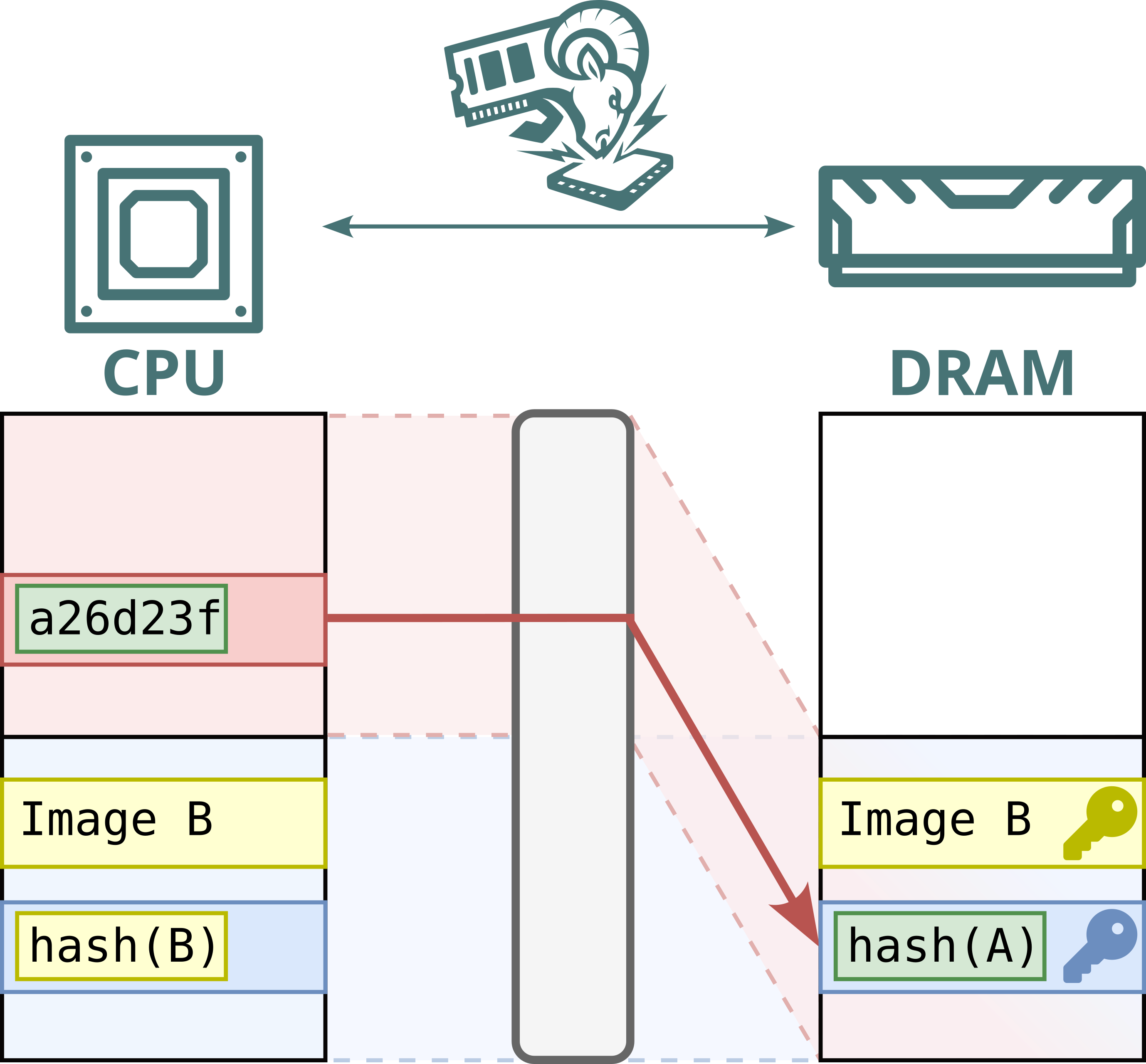
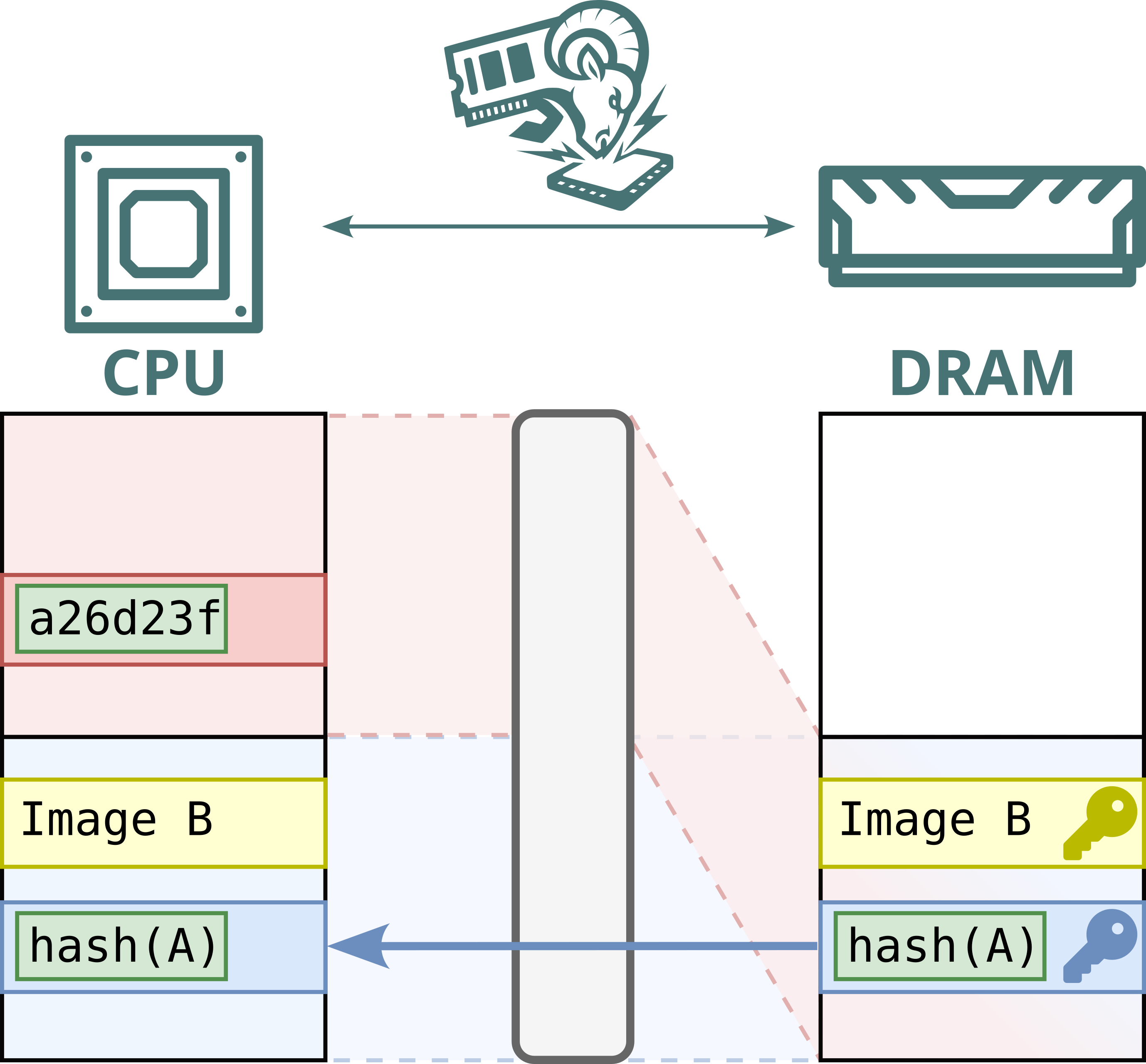
No. While Intel Scalable SGX and AMD SEV-SNP use memory encryption to protect data stored in DRAM, this encryption is static: the same plaintext at the same physical address always maps to the same ciphertext. This defends against passive attacks, such as cold boot attacks, but not against Battering RAM, which can actively corrupt or replay memory contents. Because the encryption is static, replayed data decrypts to the original value, allowing stale data to be reused.
Furthermore, Intel's memory encryption engine for DDR4 systems, TME, relies on a single key for the entire memory range. This means encryption is static, not only per address, but also shared across both attacker and victim. By replaying and capturing ciphertexts from attacker-controlled pages, the attacker can recover and inject arbitrary plaintext within the victim’s memory.
Hence, Battering RAM exposes the fundamental limits of the scalable memory encryption designs currently used by Intel and AMD, which omit cryptographic freshness checks in favor of larger protected memory sizes.
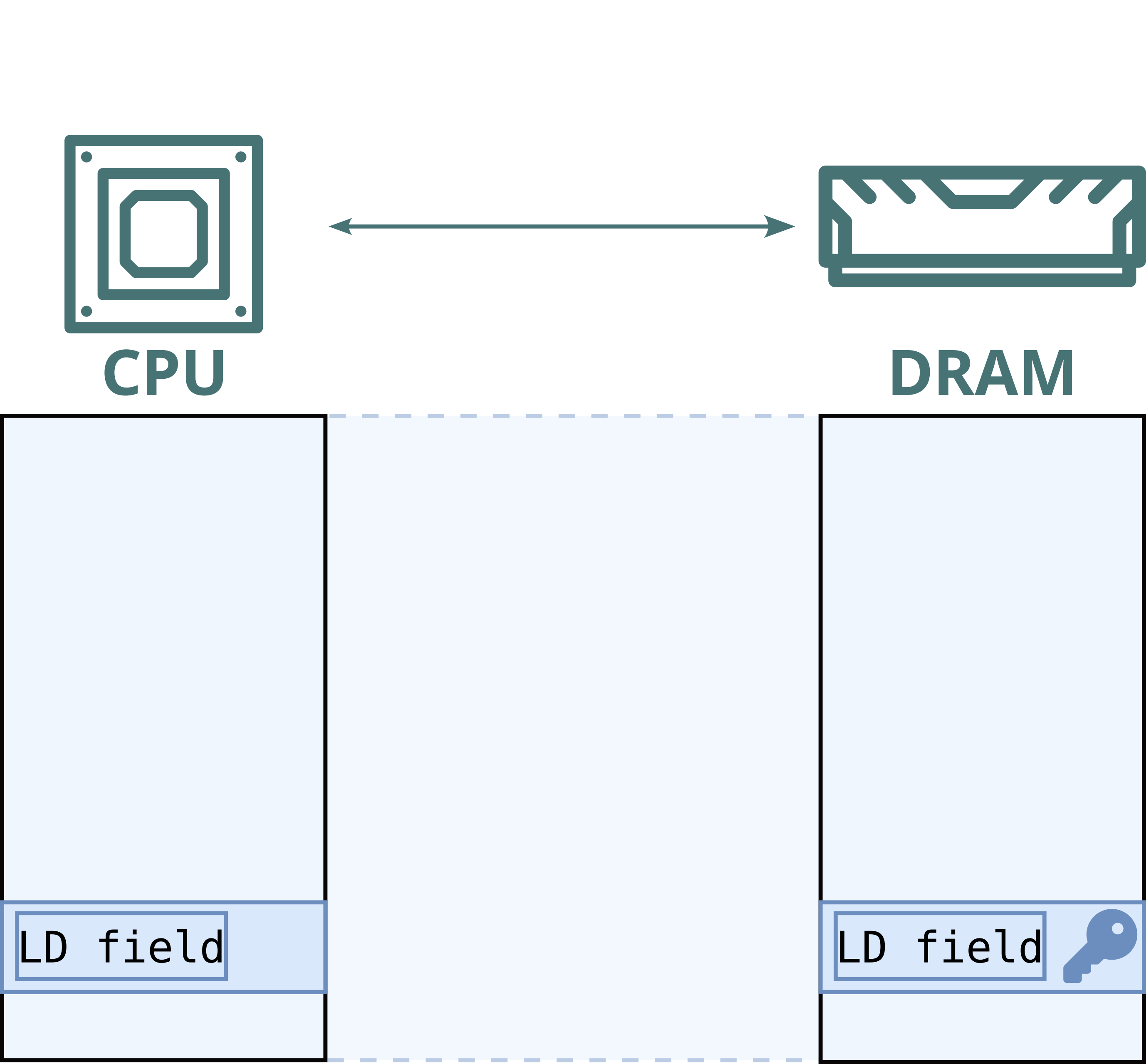
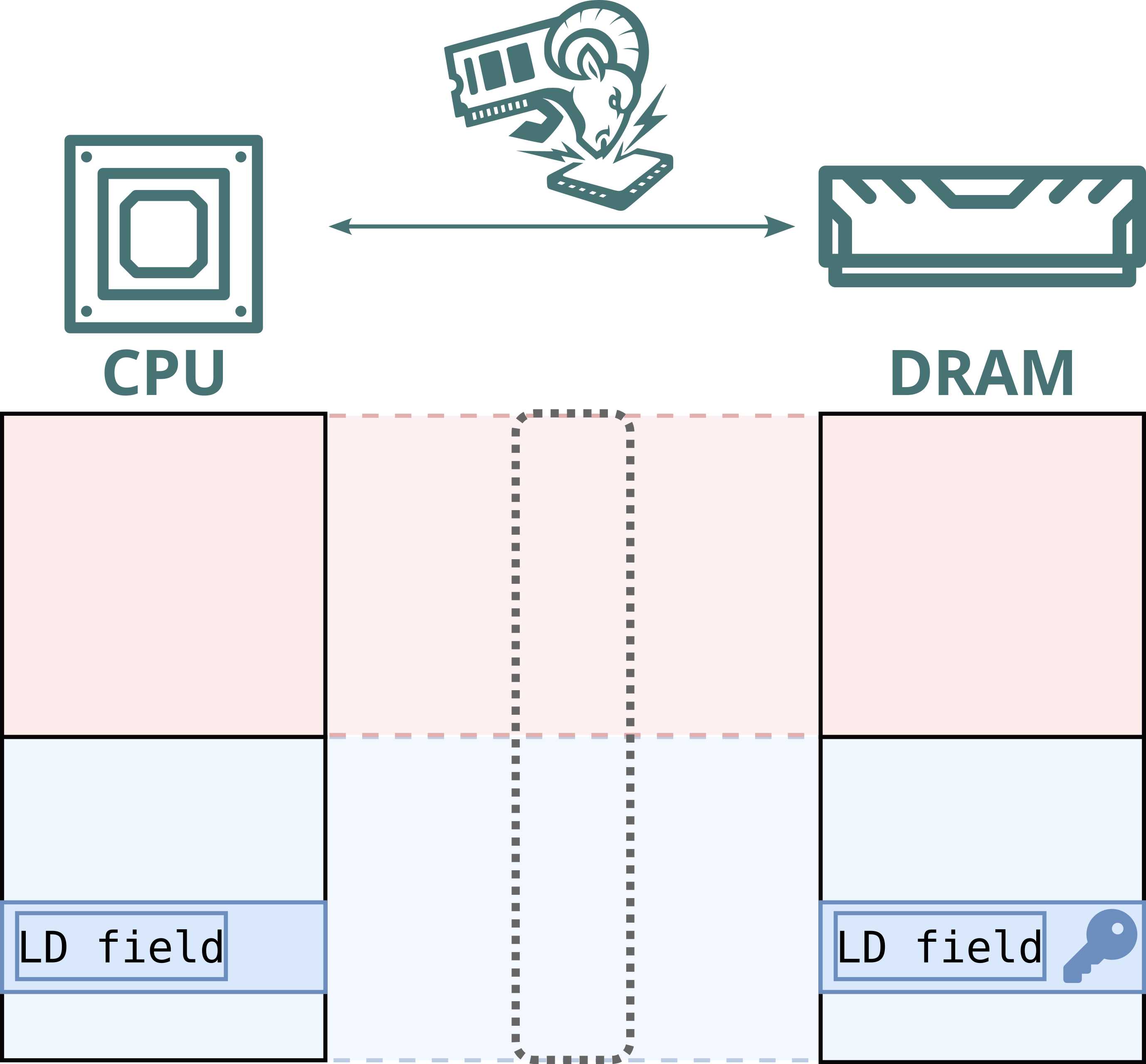
BadRAM similarly exploited physical address aliasing to modify and replay encrypted memory on AMD SEV-SNP systems. However, BadRAM relied on modifying the SPD chip on the DIMM to report a false memory size at boot time, introducing static ghost address lines. In response, Intel and AMD added boot-time checks to detect and block such static aliases.
Battering RAM, on the other hand, is capable of introducing memory aliases dynamically at runtime. As a result, Battering RAM can circumvent Intel's and AMD's boot-time alias checks.
Concurrent to our work on Battering RAM, an independent research team developed the WireTap attack, which uses a commercial DDR4 DRAM interposer to break Intel Scalable SGX. Both Battering RAM and WireTap stem from a similar attack vector, but the approaches and findings are distinct.
The key differences between these two attacks are:
- Cost: commercial DRAM interposers require specialized, high-speed signal analyzers (typically retailing at >$150,000), whereas our custom-built interposer requires only two simple analog switches and some control logic, totalling about $50. Battering RAM, therefore, shows that physical attacks are practical and not limited to resourceful adversaries with a large budget.
- Technique: Battering RAM and WireTap exploit distinct techniques: memory aliasing vs. ciphertext side-channel analysis. Commercial DRAM interposers passively capture memory traffic, requiring additional ciphertext side-channel inference to recover secrets. In contrast, Battering RAM uses a custom-built interposer that actively redirects address lines to introduce aliases, allowing not just observation but also replay and corruption of ciphertext and culminating in plaintext read/write access on Scalable SGX.
- Target: Both Battering RAM and WireTap expose the security limitations of current, scalable memory encryption technologies. Battering RAM breaks remote attestation for both Intel Scalable SGX and AMD SEV-SNP, whereas WireTap was only demonstrated on Intel Scalable SGX but may affect AMD DDR4 systems similarly.
We found that our interposer can compromise the security of two widely-deployed TEEs, Intel Scalable SGX and AMD SEV-SNP. Both of these technologies employ a memory encryption scheme that is vulnerable to memory replay attacks. Furthermore, Scalable SGX on DDR4 platforms only employs a single memory encryption key for the entire physical memory space. We show this limitation can be exploited to create an arbitrary plaintext primitive. This severely undermines the protections in the presence of a physical adversary.
On top of that, our interposer re-enables the previously-mitigated BadRAM attacks. To combat this threat, AMD rolled out firmware-level mitigations that scan for aliases at boot time. As the interposer can enable and disable the interposer at runtime, these checks are easily bypassed. As a result, Battering RAM re-enables previous attacks on AMD SEV-SNP and Intel Client SGX .
Arm has also announced a cloud TEE called CCA . Based on the specification, DDR4 systems may also be vulnerable to Battering RAM. However, as no hardware is available yet, we were unable to test our interposer on CCA.
The table below summarizes our findings across different TEEs. Each column indicates whether we were able to read, write, or replay ciphertexts, and read/write plaintext in protected memory regions.
| TEE | Read | Write | Replay | Plaintext |
|---|---|---|---|---|
| Intel Scalable SGX | ||||
| AMD SEV-SNP | ||||
| Client SGX | ||||
| Intel TDX | ||||
| Arm CCA |
No, our interposer only works on DDR4, which remains widely deployed today; e.g., a recent market study indicates that DDR4 still accounted for around 65% of sold DRAM modules in 2024.
DDR5 reorganizes the command/address bus, which removes the possibility of adding simple switches to the address lines. However, the underlying issue is not fixed, as current memory encryption engines still do not provide freshness guarantees. A determined attacker could theoretically still design more advanced interposers to perform similar attacks on DDR5.
Yes, our GitHub repository contains the hardware schematics and board files for the custom DDR4 interposer, firmware for the microcontroller, and proof-of-concept code for all attacks described in our paper. The interposer can be built for under $50, and the bill of materials is listed above.
We disclosed our findings to both Intel and AMD in February 2025. Both vendors have acknowledged our findings, but noted that physical attacks on DRAM are out of scope for their current products. To better reflect this position, Intel deposited the whitepaper on Scalable SGX, previously removed from the Intel website, permanently on arXiv.
Following an embargo period until September 30, 2025, both vendors have issued a public security advisory: Intel advisory | AMD advisory
-
Confidential computing is here, but is not invincible.
Despite strong adoption by major CPU vendors and cloud providers, current technologies have critical physical-layer limitations that remain underexamined.
-
Reevaluate your threat models.
Encrypted memory is not inherently secure against physical tampering, and firmware-based mitigations alone are insufficient in threat scenarios involving limited physical access, such as malicious insiders or supply-chain compromises.
-
Advanced physical attacks are accessible at low cost.
Our open-source $50 custom device costs only a fraction of commercial DRAM interposers (upwards of $100,000) and is capable of breaking multi-million-dollar cloud security technologies from Intel and AMD.